Shortcuts #
B – Personally Owned Equipment and ‘Bring Your Own Device (BYOD)
C – Considerations for Non University, Personally Owned Equipment and BYOD
D – Monitoring BYOD and Non University Equipment
E – Why does the University allow the use of Non University devices and BYOD
F – Differentiating services based on the relative risk of the device being used to access them
G – Mobile Device Management (MDM) mechanisms and tools
H – MDM, Registration and deregistration
I – Requirements for the use of Personally Owned, Non Universuity Equipment and BYOD
J – How to configure your device to meet the security requirements
A – Introduction #
This document should be read in conjunction with the University’s Electronic Information Security Policy (EISP) and other privacy guidance[1]. This document supports the EISP, and provides additional guidance for where non standard, non University and personally owned devices are used to access and process University data.
The University is regulated and monitored for compliance with (for example; UK Data Protection legislation and by international copy right law). Anyone studying or working on any matter relating to the University, or using the University’s technology is deemed to be an agent of the University. All agents of the University must maintain their awareness of the prevailing and underlying intentions of the University’s policies, the regulatory framework, and the collective legal and ethical responsibilities of working in an organisation, potentially where there may be vulnerable adults and those under 18 years of age.
The aim of the EISP is to guide users in how to comply with data protection legislation and protect University information, particularly that which is personal and sensitive information, from unauthorised access, dissemination, alteration, or deletion.
Compliance with the EISP is important in protecting the user themselves from harm to their work circumstances and device, but also pays particular attention to the (statutory) obligations to protect other people the user may collaborate with, or those whose other people whose data a user has access to, from any risks from the user’s awareness, devices and methods.
Using devices in the Halls of Residence (HoR) is slightly different to using devices in the University’s campus networks, although all of the good-practices and behaviours mentioned in the EISP do still apply. The HoR network, and the University’s campus network are not connected, and the HoR internet service is provided by an external company called Glide. The University works collaboratively with Glide and we apply the same safeguarding ethos and support for this as we do the University’s Campus Network – please see the ESIP, for the sorts of behaviours that are expected, and the sorts of behaviours that you should avoid. The reason for this separation is that the Univesity’s campus network also contains systems and data that is required to be strongly protected, including through UK Data Protection legislation. The mechanisms and rules regarding this level of protection mean that any (including personal) devices that are used must meet certain standards. However, the HoR network does not have as many restrictions, and therefore unlike for the University campus network, in the HoR, your device will not be overseen by ‘Mobile Device Monitoring’ and it does allow for example for gaming consoles and some Internet of Things (IoT) devices.
B – Non University, Personally Owned Equipment and Bring your Own Device (BYOD) #
Bring Your Own Device (BYOD) is a term often commonly used to refer to any, non-standard, non University managed, electronic devices owned, leased, or operated by an employee, contractor, affiliate or student of the University which is capable of storing data and connecting to a network. These include for example; mobile phones, smartphones, tablets, laptops, personal computers, netbooks and IoT (Internet of Things) devices.
The term BYOD applies to equipment not owned by the University’s IT Service. This equipment may be personally owned by you, or may be that which is provided to you by an employer, friend or relative. BYOD also applies to equipment procured by University departments other than the IT Service.
C – Considerations for Non University, Personally Owned Equipment and BYOD #
The increasingly interconnected home, on-campus and private lives opens the temptation to use a single device across the conflictions of a regulated work context with statutory obligation and consequences, and the freedoms expected in a non-work environment/context. These devices are sometimes shared with relatives, and other household members, or professional acquaintances outside of the University. Sometimes the device is shared across multiple professional roles with different employers.
However, even where used solely for work purposes, personally owned devices used for work or research purposes pose a high security risk to the University, as they may not have the in-built standards, maintenance and security utilities required for connecting to a University. It is important to realise that these risks are evolving on a minute by minute basis.
BYOD and Personally Owned devices pose a range of threats, including untraceable exfiltration and credential hijack, and are more difficult to manage if the devices were to be stolen or lost. BYOD and Personally Owned devices present an additional data storage challenge, as the data stored on these devices is not protected by the University’s centralised storage and data backup technologies.
It is also the case that a University device used for unapproved, non-work purposes is high risk. University devices whilst protected with the prevailing industrial strength, market leading security products cannot avoid some of the risks associated with personal use.
Copying University data to personally owned, and departmental procured devices also reduces the ability for the University to know where University data is stored and makes it harder to comply with relevant legislation. The use of unmanaged personally owned devices to access University data may also be prohibited by contracts or agreements in place between the University and third parties.
University data held on personally owned devices is subject to the Freedom of Information Act and the Data Protection Act and must be processed in compliance with information related legislation and associated University policies.
Not all BYOD and Personally Owned devices are compatible with the University’s IT environment. Some devices may not have the capability to connect to our systems. Unless there is a formally agreed business case to do so, there will be no modification made to University systems to assist non University equipment to connect.
D – Monitoring BYOD and Personally owned Equipment #
As set out in the University’s privacy standard[1], the University does not monitor the content or use of your personal devices[2]. however, the University reserves the right to monitor and log data traffic transferred between your device and University systems, both over internal networks and entering the University via the Internet.
In very exceptional circumstances, for instance where the only copy of a University document resides on a personal device, a cyber or information security incident, or where the University requires access in order to comply with its legal obligations (e.g. under UK Data Protection Legislation and the Freedom of Information Act 2000, or where obliged to do so by a law enforcement authority) the University will seek your support in resolving an issue with University information stored on your personal device.
[1] See https://help.chi.ac.uk/docs/privacy-and-monitoring and https://www.chi.ac.uk/about-us/policies-and-statements/data-protection/
[2] The University does not for example collect web browser history on a BYOD when not connected to University network(s), unless the web traffic is directed through the University’s network infrastructure.
E – Why does the University allow Non University, Personally Owned Equipment and BYOD #
As it is necessary to have an open architecture to enable students etc, the University’s IT systems already have password protection, and a range of security mechanisms ‘patrolling’ to safeguard systems, information and people from unauthorised access.
It is also a fact of life that a University has a very broad federation of stakeholders, across research, and affiliations, partnerships etc. There has therefore to be a balance between perimeter security (i.e. you can not access under any circumstances) and logical, layered security throughout the whole of the University’s IT ecosystem.
The Provisioning Policy[1]. sets out the arrangements for equipping staff appropriately to their role, and work and a range of open-access and loan equipment is available where there are circumstances such as individuals that do not work exclusively for the University, or may need to work off-campus. This might be for example those that work as Associate Lecturers who may need to use a non-University device from time to time. Similarly, the University does not provide a University device to for example external examiners and other partners.
Staff that use a personal device therefore join students, suppliers and partners in using a device that may have a lesser protection to the statutory entitlement of other University stakeholders, and that is less than what is expected within the regulators expectations of a secure organisation. The consequence of this reality, is that regulators therefore expect there to be safeguarding mechanisms that reflect the device(s) used, as well as the user’s role in allowing or disallowing access to more or less sensitive data.
BYOD can be a complex set of variations – It is important to recognise that its commonplace for a University’s information services to be accessible via the Internet, where they are protected by passwords etc. This ‘capability’, means that you may have multiple devices, (University provided and not) through which your work. For example sometimes accessing your email on your University provided laptop, and sometimes via your personal mobile phone or tablet.
If employees have been supplied a device by the University’s IT department, the preference should be to use this as the default device for business purposes rather than use a BYOD or any personally owned equipment.
F – Differentiating services based on the relative risks of the devices used to access them #
Across the range of user and device scenarios, there is a regulatory requirement for ensuring ‘end to end’ security, including the potential need to evidence that no unauthorised infiltration or exfiltration has occurred.
As noted above, BYOD therefore becomes a factor in allowing or disallowing access to more or less sensitive data and situations. The HE sector, and this University have therefore begun to deploy a additional security mechanisms. These are often referred to as Mobile Device Management (MDM) solutions, which has a number of variations and ways in which it might be configured (see below).
G – Mobile Device Management (MDM) mechanisms and tools #
In its most simplistic form, a BYOD or user of a personally owned device will register their device in an automated (one-off) MDM e-form. This helps identify the internal identity of the device to the registered user when it is used to access University systems and services.
In a more sophisticated form, MDM software will interrogate the device each time it tries to connect to the University, assessing the devices for the presence of malware, how well the devices security is configured, and absence of up to date safeguarding. Access to the University;’s Multi-factor-login mechanisms will only be granted if the device meets the MDM standards set out by University.
In a more advanced form, where MDM approves the device to access only low risk services, whilst also monitoring for any aberrant activity.
In is ideal form; MDM will download local software to the device to create a private (encrypted) session between the BYOD and the University, allowing the same level of access as is afforded to a University device, using multi-factor-authentication, but ensuring there can be no exfiltration.
MDM does not prevent the installation of software or applications on your BYOD. However, the University may block access to University ICT services if detects that any of your software, applications, device configuration, or data present a threat to the University.
It is important to recognise that access to University systems and data (irrespective of how, or through what device) is enabled at the discretion of the University and access may be revoked at any time and for any reason.
H – MDM, registration and de-registration #
The EISP[1] sets out the policy for access to University systems and services. As set out above, BYOD requires conscientious, expert, management by the user, and exposes additional risks, due to the temptation to blend work, and non work situations and activity. MDM is used to support the expertise of BYOD users, and help them achieve the integrity inherent in University provided equipment.
As it is related to the network login (itself related to current status as an employee/student) planned de-registration happens automatically in the case of someone who leaves. It is intended that this automation will be extended to deinstalling any local MDM software, along with any local University data. Users may also deinstall any University MDM software. Re-registering, or registering a new device is straight forward, as it is also related to the (Multi-Factor-Authentication protected) network login, and is combined with the facility to install the MDM software.
Although it suspension from access would typically only be used in conjunction with a wider security situation, MDM will exclude any device that poses a threat, and access may in any case be suspended after a period of disuse.
I – Requirements for the use of Non Universuty, Personally Owned Equipment and BYOD #
BYOD users are required to;
- Enable the University to install and update MDM facilities on their BYOD, and give permission to the University to wipe the BYOD in the event of loss or disposal[1].
- Ensure the device is not counterfeit, rooted, or jail-broken,
- Install and maintain approved, up-to-date virus protection software and digital certificates necessary to maintain security,
- Ensure they know the whereabouts of the BYOD device, and adequately secure the device from loss or theft[2],
- Store information in suitable media, as set out in the additional guidance set out in the EISP,
- Ensure there is no risk of any personal data described as Unauthorised in the EISP becoming associated with the University, or being used to compromise the University,
- Ensure there are no automated synchronisations with local or cloud backup is disabled to ensure that University data is not inadvertently leaked, compromised or mishandled,
- Not allow any other users (family members for example) to use the device,
- Create separate University and personal log-in accounts on the device, ensuring there are no shared facilities such as storage and email,
- Ensure the device has separated accounts, and that no-one user, can use another user’s device account, and that there are is storage (local or cloud) that transcends device accounts,
- Apply a login code with an acceptable level of complexity to enable secure access to the device,
- automatically locking the device after an inactivity timeout period,
- Encrypt all data stored on the device,
- Apply a time-out device lock, and appropriately strong PIN/Password hygiene,
- Ensure they have their own technical support for their BYOD[3],
- Ensure appropriate current licencing for operating systems and applications running on a BYOD, and
- Ensure that they do not use a common email client for private and University email accounts.
In the event that any device that contains University data, (or that has the means to access University services) is lost or stolen, this must be reported to SIZ immediately.
J – How to configure your device to meet the security requirements #
BYOD users are required to;
Keep your operating system up to date
In general terms, you should apply the latest updates provided by your operating system manufacturer as soon as reasonably possible. This should be no less than 14 days after the update has been made available on your device. However, not all operating systems are kept up to date, as manufacturers remove support after some time.
Even if you do not use your device for work purposes, the principles above are recommended to keep your own personal information safe and secure, as Operating systems release security updates regularly.
IT Services has put together guidance on the minimum BYOD operating systems requirements across devices. This is up to date as of March 2024:
Device Type | Operating System | Minimum Supported Version | Latest Supported Version |
Desktop or Laptop Computer | Microsoft Windows | Windows 10 | Windows 11 |
Apple iMac or Macbook | MacOS | 12 (Monterey) 13 (Ventura) | 14 (Sonoma) |
iPhone or iPad | iOS iPadOS | 15 16 | 17 |
Android Phone or Tablet | Android | 12 13 | 14 |
Games Console | Varied | Not supported | Not supported |
IOT Device (eg Amazon Echo, Smart TV, Apple Watch) | Varied | Not supported | Not supported |
Desktop or Laptop Computer | Linux | Varied | Varied |
Chromebook | Chrome OS | Update every 4 weeks | |
Keep your device secure
Anti-virus
It is essential that you install anti-virus software on your device to ensure that your device is protected against threats such as malware. It is also important that this anti-virus software is kept up to date with the latest definitions updates from the manufacturer. As a rule of thumb, we recommend not letting your anti-virus software go any more than 14 days without an update.
For BYOD, the University is unable to make specific recommendations of antivirus software that is right for your operating system and device. Some are free to use, whereas others come with a cost and normally subscription based.
Below are some online resources which may help in your decision of which Antivirus software to install on your computer:
Antivirus software for staff personal devices will not be funded by the University, however, the IT Team are actively exploring home-use benefits available within existing software licence agreements, which may mean that antivirus software can be provided at no cost to staff (and potentially students).
There are free-to-use anti-virus solution to consider (examples below) that would, at the time of writing, satisfy this aspect of conditions of connecting your device to the Unirersity.
AV Comparatives: https://www.av-comparatives.org/consumer/
Tech Advisor: https://www.techadvisor.com/review/antivirus
Firewall
If your BYOD is Windows or Mac, then you will need to ensure that you have a Firewall installed and enabled. Both device types have a Firewall built in and is enabled by default. However, some anti-virus software packages come with a third-party firewall. Either way, you must ensure that your firewall is always running.
Use a Password, PIN or Biometrics.
All the supported devices above will have the option to unlock or authenticate to use the device with Password, Pin or Biometrics.
For Windows, Mac and Linux devices, you must ensure that a strong password is used to gain access to the device. The University maintains clear guidance on good password maintenance which can be found here. Biometric authentication such as thumbprint or facial recognition are also recommended in combination with a password if your device supports it.
For mobile devices including iOS, iPadOS and Android devices, you should configure your BYOD to require a PIN or Biometrics to use the device.
In combination with a Password, Pin or Biometrics, you must lock or log out of your device if you plan to leave it unattended for any duration.
Your device should be configured with a short inactivity time out before requiring your Password, Pin or Biometrics again to use the device. This should be as short as possible, and no longer than 5 minutes.
Device Specific Guidance
Below you will find links to pages which will guide you in setting up your personal device so that they are compliant with the University’s BYOD requirements:
Microsoft Windows device (Staff)
The guidance on this page applies to University staff who wish to use their personal, or unmanaged Windows device for work purposes.
As a member of staff, you will need to install the Microsoft Intune Company Portal to access University services on your Windows device. The Company Portal will grant you access to University services so long as your device meets certain criteria, as set out in the guidance for Personal Devices. It is important to review this guidance before continuing through the steps below.
Installation of the Company Portal on your personal device will not grant Microsoft or the University access to any of your personal information held on your device.
Where possible, we highly recommend using a University provided computer or device to access services. This will have the necessary security controls in place to support your working.
Before you register: #
- Make sure that you are using a personal or unmanaged Windows computer. You can do this by pressing the following combination on your keyboard: ‘CTRL + ALT + I’. If your device information is displayed, then you are using a University managed computer and should not proceed with the next steps. If your device is not working as intended, please contact the SIZ on help@chi.ac.uk.
- You will need to be running the latest version of Microsoft Windows 10 or 11 on your device with the latest security patches installed. You can review the University requirements for updates here: https://help.chi.ac.uk/docs/personal-devices#Configure. Please visit the Microsoft guidance here on how to keep Windows up to date: https://support.microsoft.com/en-us/windows/update-windows-3c5ae7fc-9fb6-9af1-1984-b5e0412c556a#WindowsVersion=Windows_11
- Is your device already registered with the University of Chichester?
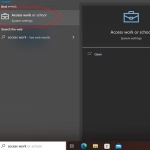
- Find and open ‘Access work or school’ from the Start Menu.
- If your identity is displayed beneath the ‘Connect’ button, then you are already registered.
- Is your device already registered with another University or organisation?
You should check with the other organisation’s IT team to determine if they will support you registering your device with another University.
- Open ‘Settings’ from the start menu and select ‘Accounts’
- Select ‘Email & accounts’ from the left-hand panel
- Under Accounts used by other apps, click ‘Add a workplace or school account’
- Follow the sign-in dialogue using your University of Chichester credentials.
Registering your device: #
- On your Windows device, install the Company Portal using the Microsoft Store: https://apps.microsoft.com/store/detail/company-portal/9WZDNCRFJ3PZ
- Click ‘Open’ in the Microsoft Store.
- You will be asked for your University email address, and then presented with the sign in procedure for your password. You will also be asked to authenticate with MFA (Multi Factor Authentication).
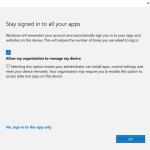
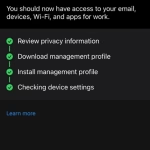
- You will then be presented with the following dialogue. Click ‘Ok’.
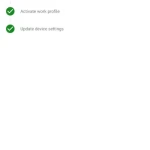
- Your Windows device will then register itself to the University. The Company Portal will continue to monitor your device to ensure that it remains compliant with the security standards set out in the Personal Devices Help Page: https://help.chi.ac.uk/docs/personal-devices.
- You will then notice the following screen once registered. Click ‘Done’.
- The Company Portal will open, and you can browse Apps that you’re entitled to install on your personal device. It is from here that you can manage your devices registration with the University.
Removing your device registration #
You can unregister your device at any time. Doing so will also remove your ability to access University services from your personal device.
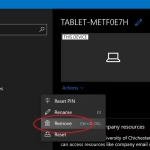
- From the Company Portal select ‘Devices’ from the left hand panel.
- Locate your device, select ‘Actions’ and then ‘Remove’.
- Your device will then be removed from your profile and you can remove the Company Portal app from ‘Apps & features’ if it is no longer required.
Android device (Staff)
The guidance on this page applies to University staff who wish to use their personal, or unmanaged Android device for work purposes.
As a member of staff, you will need to install the Microsoft Intune Company Portal to access University services on your device. The Company Portal will grant you access to University services so long as your device meets certain criteria, as set out in the guidance for Personal Devices. It is important to review this guidance before continuing through the steps below.
Installation of the Company Portal on your personal device will not grant Microsoft or the University access to any of your personal information held on your device.
Installing the Company Portal on your Android device will create a dedicated profile for University services.
Where possible, we highly recommend using a University provided computer or device to access services. This will have the necessary security controls in place to support your working.
Before you register: #
- Make sure that your device is not alreaday managed. You can determine this by checking if the Company Portal app is present on your device, and upon opening the app you will see your device listed.
If your mobile phone was provided to you by the University, then you will have the Company Portal configured already and you do not have to follow this guidance any further.
If your device is enrolled, but not working as intended, please contact the SIZ on help@chi.ac.uk. - You will need to be running a supported version of Android, with the latest security patches installed. You can review the University requirements here: https://help.chi.ac.uk/docs/personal-devices#Configure.
Guidance on updating your Android device will differ between various device manufacturers. If in doubt, please visit the Google guidance on how to keep your Android device up to date: https://support.google.com/android/answer/7680439?hl=en-GB - Is your device already registered with another University or organisation?
You should check with the other organisation’s IT team to determine if they will support you registering your device with another University. - Remove all apps that uses your University network account. This will include Outlook, OneDrive, Word, Teams, etc. You will be able to reinstall these later. Failure to uninstall them now may render them unusable on your device.
Registering your device: #
- On your Android device, install the Microsoft Intune Company Portal app from the Google Play store:
Note: If your Android device does not have access to the Google Play store, then it is unlikely to be compliant with the Personal Device security requirements listed here: https://help.chi.ac.uk/docs/personal-devices#Configure - Open the Company Portal app on your Android device. If prompted, allow Company Portal to send you notifications.
Note: Preventing notifications may give you a degraded experience, and you may miss important information about your devices ongoing compliance with University security requirements. - At the homepage, tap ‘Sign In.’
Enter your University email address, tap ‘Next’ and continue to authenticate using your password. You will be prompted to authenticate with MFA.
The Company Portal will attempt to register your device. - You may be presented with a ‘Company Access Setup’ page, tap ‘Begin’ to continue.
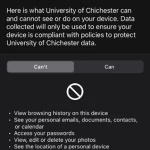
You will be shown a privacy notice about what the app will and will not have access to. In this case, the University will not have access to your Mobile Phone Number.
Tap ‘Continue’ if you are satisfied with this notice. - Your device will then register itself to the University. The Company Portal will continue to monitor your device to ensure that it remains compliant with the security standards set out in the Personal Devices Help Page: https://help.chi.ac.uk/docs/personal-devices
- Your Work Profile will be set up on your phone. These steps will vary depending on your device manufacturer. Proceed through the steps as shown on your device.
- Your Work Profile will be created, you will now have to Activate it by tapping ‘Continue’.
- If all has gone well, you should be presented with a ‘You’re all set’ screen. Tap ‘Done’ to dismiss this message.
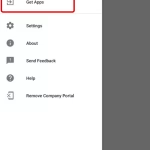
- You can now begin installing University Apps in your new ‘Work Profile’. The easiest way to do this is by opening the ‘Company Portal’ app under your Work Profile, and select ‘Get Apps’.
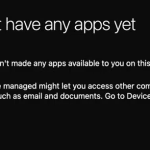
- You will be taken to the University’s app store where approved apps can be downloaded on to your Work Profile.
The following video shows the enrolment process:
Removing your device registration #
You can unregister your device at any time. Doing so will also remove your ability to access University services from your personal device.
- In a web browser, navigate to https://byod.chi.ac.uk. Proceed to authenticate with your University network account. From the Company Portal select ‘Devices’ from the left hand panel.
- Locate your device, select ‘Actions’ and then ‘Remove’.
- Your device will then be removed from your profile and you can remove the Company Portal app from your Android device.
You will receive a notification on your device that your ‘Work Profile’ has been deleted.
Apple Mac device (Staff)
The guidance on this page applies to University staff who wish to use their personal, or unmanaged Apple Mac device for work purposes.
As a member of staff, you will need to install the Microsoft Intune Company Portal to access University services on your device. The Company Portal will grant you access to University services so long as your device meets certain criteria, as set out in the guidance for Personal Devices. It is important to review this guidance before continuing through the steps below.
Installation of the Company Portal on your personal device will not grant Microsoft or the University access to any of your personal information held on your device.
Where possible, we highly recommend using a University provided computer or device to access services. This will have the necessary security controls in place to support your working.
Before you register: #
- Make sure that you are using a personal or unmanaged Apple Mac. If you are using a University managed device you should not proceed with the next steps. If your device is not working as intended, please contact the SIZ on help@chi.ac.uk.
- You will need to be running a supported and up to date version of MacOS on your device with the latest security patches installed. You can review the University requirements for updates here: https://help.chi.ac.uk/personal-devices#Configure. Please visit the Apple guidance here on how to keep MacOS up to date: https://support.apple.com/en-gb/guide/mac-help/mchlpx1065
- Is your device already registered with the University of Chichester?
- Open the Apple Menu, and open ‘System Settings’
- Under ‘Privacy and Security’ check to see if a Management Profile is already installed. If so, you should not proceed with the next steps.
- Is your device already registered with another University or organisation?
If so, you should check with the other organisation’s IT team to determine if they will support you registering your device with another University.
Registering your device: #
- On your Mac, open a web browser and open the following URL:
https://byod.chi.acuk
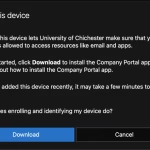
You will be prompted to sign-in with your University network account. - Select ‘Devices’ and then ‘Add this one by tapping here’
- When prompted to do so, agree with the dialogue to download and install the ‘Company Portal’
- When prompted, allow downloads from portal.manage.microsoft.com
- When prompted, accept the data notice to allow MS Auto Updater to update the Company Portal app.
- Launch the Company Portal. You may have to navigate to ‘Applications’ in order to do this.
- Sign-in with your University network account.
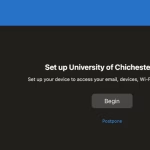
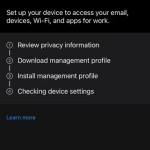
- When prompted with ‘Set Up University of Chichester Access’ select ‘Begin’
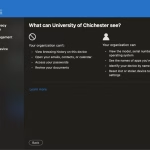
- You will be shown a notice which gives you information on what information the Company Portal has access to. Review this, and select ‘Continue’
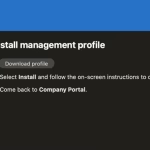
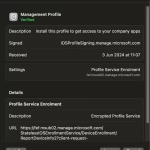
- You will now need to install a Management Profile. From select ‘Download profile’ when prompted
- If the Profiles window doesn’t open automatically, open the Apple Menu, and open ‘System Settings’
- Under ‘Privacy and Security’ check to see if a Management Profile ready to be installed. Double Click the Management Profile to install it
- Review the Management Profile information and select ‘Install’
- Return to the Company Portal, it will continue to perform a compliance check. Intune will perform these regularly to ensure that your device meets the requirements in order to access University services.
- Once complete you should see a ‘You’re all set’ message. Click ‘Done’
Removing your device registration #
You can unregister your device at any time. Doing so will also remove your ability to access University services from your personal device.
- From the Company Portal select ‘Devices’ from the left hand panel
- Locate your device, select ‘Actions’ and then ‘Remove’
- Your device will then be removed from your profile and you can remove the Company Portal app if it is no longer required.
Apple iOS or iPadOS device (Staff)
The guidance on this page applies to University staff who wish to use their personal, or unmanaged Apple iOS or iPadOS device for work purposes.
As a member of staff, you will need to install the Microsoft Intune Company Portal to access University services on your device. The Company Portal will grant you access to University services so long as your device meets certain criteria, as set out in the guidance for Personal Devices. It is important to review this guidance before continuing through the steps below.
Installation of the Company Portal on your personal device will not grant Microsoft or the University access to any of your personal information held on your device.
Where possible, we highly recommend using a University provided computer or device to access services. This will have the necessary security controls in place to support your working.
Before you register: #
- Make sure that your device is not already managed. You can determine this by checking if the Intune Company Portal app is present on your device, and upon opening the app you will see your device listed.
If your mobile phone was provided to you by the University, then you will have the Company Portal configured already and you do not have to follow this guidance any further.
If your device is enrolled, but not working as intended, please contact the SIZ on help@chi.ac.uk.
- You will need to be running a supported version of iOS or iPadOS, with the latest security patches installed. You can review the University requirements here: https://help.chi.ac.uk/docs/personal-devices#Configure.
If in doubt, please visit the Apple guidance on how to keep your iOS or iPadOS device up to date: https://support.apple.com/en-gb/118575.
- Is your device already registered with another University or organisation?
You should check with the other organisation’s IT team to determine if they will support you registering your device with another University.
- Remove all apps that use your University network account. This will include Outlook, OneDrive, Word, Teams, etc. You will be able to reinstall these later. Failure to uninstall them now may render them unusable on your device and you will have to re-install later.
Registering your device: #
- On your device, install the Microsoft Intune Company Portal app from the App store:
https://apps.apple.com/gb/app/intune-company-portal/id719171358 - Open the Intune Company Portal app on your device.
- At the homepage, tap ‘Sign In.
- Enter your University email address, tap ‘Next’ and continue to authenticate using your password.
- You will be prompted to authenticate with MFA.
- The Company Portal will attempt to register your device.
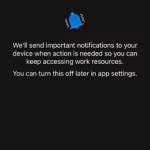
- If prompted, allow Company Portal to send you notifications.
- Note: Preventing notifications may give you a degraded experience, and you may miss important information about your devices ongoing compliance with University security requirements.
- You may be presented with a ‘Setup University of Chichester access’ page, tap ‘Begin’ to continue.
- You will be shown a privacy notice about what the app will and will not have access to.
- In this case, the University will not have access to your Mobile Phone Number.
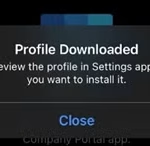
- Tap ‘Continue’ if you are satisfied with this notice.
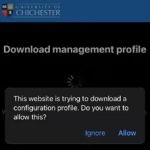
- Your device will then attempt to download a Management Profile to your device.
- You will be prompted to allow this, tap ‘Allow’.
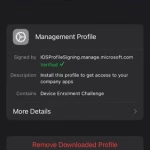
- You will now have to open ‘Settings’, followed by ‘General’ and then ‘VPN & Device Management’. An option should appear under ‘Downloaded Profile’.
- Tap ‘Management Profile’ and then ‘Install’.
- Review the certificate warning and select ‘Install’ again to trust the certificate warning if shown.
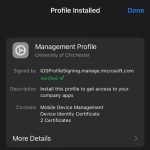
- The profile should install, tap ‘Done’
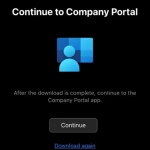
- Switch back to the Company Portal app.
- Now that you have the profile installed on your device, tap ‘Continue’
- Review the checklist. Tap ‘Done’
- The Company Portal will continue to monitor your device to ensure that it remains compliant with the security standards set out in the Personal Devices
- Help Page: https://help.chi.ac.uk/docs/personal-devices
- You can now begin installing University Apps from the Company Portal App. The easiest way to do this is by opening the ‘Company Portal’ app and tap ‘Apps’.
The following video shows the enrollment process.
Removing your device registration #
You can unregister your device at any time. Doing so will also remove your ability to access University services from your personal device.
- In a web browser, navigate to https://byod.chi.ac.uk. Proceed to authenticate with your University network account. From the Company Portal select ‘Devices’ from the left-hand panel
- Locate your device, select ‘Actions’ and then ‘Remove’
- Your device will then be removed from your profile and you can remove the Company Portal app from your device.
Staff FAQ
What data will the University have access to on my personal device? #
Installation of the Company Portal on your personal device will not grant the University access to any of your personal information held on your device.
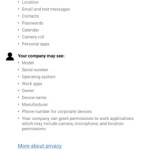
The University may have access to:
- Device Model
- Device Serial Number
- Device Operating System
- Work Apps
- Owner
- Device Name
- Manufacturer
- Phone number (corporate devices only)
The University will not have access to:
- Call and web history
- Location
- Email and text messages
- Contacts
- Passwords
- Calendar
- Camera roll
- Personal apps
[1] The University does not accept responsible for any personal loss or damage suffered as the result of actions undertaken by the University to protect University data stored on a BYOD.
[2] See EISP, but also, this should include installing tracking and/or wiping services, such as Apple’s ‘Find My’, Android’s ‘Where’s My Droid’ or Windows ‘Find My Phone’.
[3] The University will only provide best effort support for any applications that the University has provided, and for network connection troubleshooting.