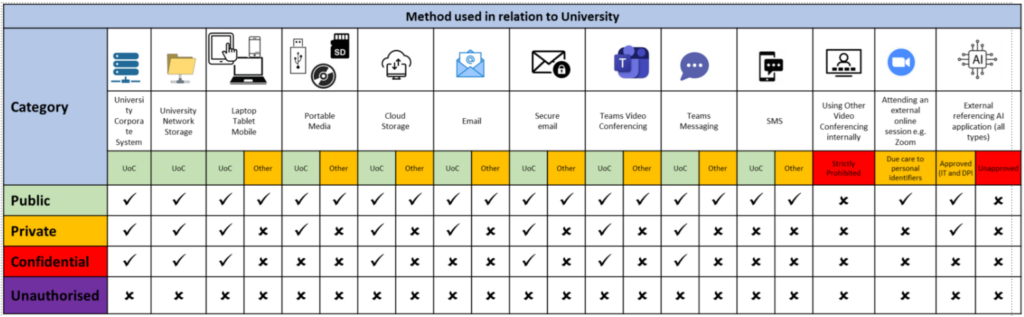
In the context of the University, there are four main classes of information which may affect some or all students, staff and visitors and partners:
Category – PublicThis is data that is carefully considered to ensure that its disclosure causes no harm to individuals, the University, or its various suppliers and partners. This is typically general data / information that can appropriately be viewed by anyone, anywhere e.g. press releases, course information, publications, released research data, conference papers etc. | |
Category – Private | |
Category – Confidential (Protected Characteristics and Sensitive Personal Information)This is information that, if disclosed, would be a failure to protect an individual’s statutory rights. Data Protection legislation identifies that statutory responsibilities apply where you (individually and / or as part of an organisation) have a copy of information relating to another person. This can be any data which identifies an individual, directly or by inference, either on its own or by reference to other information and can include expressions of opinions about an individual or for example photographs of them. Such personal data requires the strongest possible technical safeguards and clearly defined processes to ensure it cannot be seen by anyone not authorised to do so. Additional measures may also be required when processing special category data. Examples of personal data include: Personal Identification Information – PII
Special category data includes:
Any piece of information which contains any of the above must be processed in compliance with data protection legislation. This would include for example, student assessments either because it identifies them or, where in conjunction with other information the student can be identified. Confidential information should only be stored in University case management systems or University network storage. Using removable media, or storing any private information on a laptop, personal device or using personal cloud storage is strictly prohibited | |
Category – Unauthorised | |
Information Labelling
In the context of files and folders, these are identified to who creates or stores them.
In the background, all data is always treated as though it is highly confidential, and the maximum security mechanisms within the University’s infrastructure design are applied.
You may wish to visibly identify that something is sensitive (confidential or private for example), to anyone you might share this information with. This might be through headers and footers in documents, watermarks, or by attaching a meta-tag.
You may additionally wish to make anything particularity sensitive ‘read-only’ when shared and use password protection. NB, it is good practice to send the pass code separately to any sharing notification.
It is generally better not to include words such as confidential in folder or files names, as in a worst case scenario, this might signpost an unauthorised infiltrator what is of most value to steal.
- It is better to create a SVOT (Single Version of the Truth) and to share a link to it, rather than duplicate, print or send copies that can become misplaced, or out of date.
Information security & devices and storage
For confidential information, case management systems with their inherent access controls and their data management facilities should be used wherever possible. Where this is not possible, network storage is the most secure ad-hoc storage.
- Log off from any active sessions, terminate services when no longer in use, and lock away your equipment when not in use
Local Device Storage
- Storing any private or confidential data on a laptop, Mobile phone or PC’s ‘hard drive’ (local, inbuilt, often referred to as C:) facilities, or any other in-built storage such as an SD card is very high risk, susceptible to loss, and may be easier for criminals to access if they gain access to your device – please use the network and cloud storage we have made available. The policy is that all private and confidential information should be stored in case management or University network and cloud storage.
- You should ensure a clean-desk approach in relation to any University information or activity whether working in a University location, or working at home or elsewhere.
- It is important, and polite not to leave any discarded papers in classrooms or other public spaces
- Clean Screen policies identify that you should not store any private or confidential data on the desktop screen of your computer – as this is especially high risk to covert unauthorised access and cyber criminal attack.
- Please note that only leaving a computer in ‘sleep’ or standby increases the risks of unauthorised access – please fully power off the device
Network Storage
- Home drives: (H:) All students and staff have access to network storage known as their home drive or H: drive. This is secure network storage for personal University data attached to their network account, which can be securely accessed from any computer or device connected to the Internet.
- Shared drives: (S:) and the University’s One Drive For Business (ODFB). There are additional network storage called shared drives (or S: drive). This network storage is linked to groups of network accounts enabling users to collaborate and share files.
- Advantages of using University Network Storage: The University’s network storage can be used for Private and (where not possible to be stored in a case management system), confidential information. Data is protected by University information security systems. Data is routinely backed up for business continuity purposes as well as to enable the recovery of data that is accidentally deleted.
Portable Devices
- University Issued Devices: Portable devices (such as laptops, tablets and smartphones) may be issued/loaned to enable access University resources whether at a desk, or on the move. Security measures are installed, and data is directed to network storage.
- Personal Devices: The University enables access to University systems and services through a staff, student or visitor’s own device. Access is controlled through authentication to each system or service. Users also have a responsibility to ensure their devices are protected, e.g. use a boot password, a screen saver with a password, disk encryption and anti-virus software, even if you only ever access public data. You must not download private or confidential data to a personal device.
- Working off campus: Please remember to exercise extra caution when connecting to 3rd party wireless networks (at home, in a coffee shop or hotel for example). Any WiFi which does not require authentication via a user ID and password should be regarded as risky and non-secure.
- If you need to leave equipment temporarily you should log-out, lock the screen (put the device to sleep, and ideally fully power off the device), as well as ensuring it is physically secured (most laptops can be leash locked, and leash locks can be loaned from SIZ)
Portable Storage
- University Issued Storage Media: Portable storage media (CDs/DVDs, SD Cards USB drives and external hard drives) are discouraged. Security measures (such as encryption software) are used to help reduce the risks, however due to the risks of their being lost, portable storage media are not suitable for storing confidential information.
- Personal Storage Media: The University does not currently restrict the use of personal storage media; however, their use for private and confidential University data is not permitted.
- Mobile Telephones: Data on mobile phones cannot easily be backed up. Mobile phones can be lost or stolen and have very little security. They must not be used to store private or confidential data
Considerations when using Portable Devices and/or Storage Media
- Files stored only on portable devices and/or storage media have no provision for backup or recovery if they become lost, stolen or corrupted.
- It would be extremely high risk to reuse portable media, or to try recycling such media from a previous user.
- There is a significant risk of reputational damage and/or litigation and fines if data is stored inappropriately on portable devices, especially when it could have been stored in network storage.
- Portable devices and local storage on a PC / laptop, and personal devices must not be used for Private or Confidential information
- If it cannot be avoided, any data that has to be temporarily copied to portable media must be encrypted, using a storage device obtained through the University’s SIZ.
- Following such use, this media must be returned to SIZ for secure cleaning and disposal.
- Personal devices/storage media, including personal email accounts must not be used to store private and confidential data.
- NB USB sticks, and CDs and SD Cards etc can degrade over time
- Portable media should be handed in to SIZ for secure disposal
- Any removable media used for temporary storage should be protected with suitable encryption and locked in a known, safe location that is free from risks of humidity, dust, heat etc.
Cloud Storage
- University Cloud Storage: All staff and students have access to the University’s cloud storage system – OneDrive for Business. One Drive for Business (ODFB) provides cloud storage (in a data centre in the UK) which can be accessed on and off campus. ODFB should not be used for confidential data, (and networked H / S storage ideally should be used).
- MS Teams is the University’s collaboration platform, and this is also a cloud storage facility, through which you can securely share documents with other colleagues and students
- Other Public Cloud Storage: Other cloud providers, such as Dropbox, iCloud, we-transfer Google docs etc should not be used. The services offered by these providers cannot be protected.
Considerations when using Cloud storage:
- University OneDrive for Business is protected by industry standard security systems, where if/what/when can be confirmed by the University and even files you delete are recoverable (for up to 90 days).
- Creating a shareable document (Single Version of the Truth) helps increase security, and accuracy of information.
- Private and confidential data must not be uploaded to any personal cloud storage service.
- Synchronisation between ODFB and non University devices must be turned off for all categories of data.